
Cyber Battle of Nordic-Baltics – self-study portal
This year you can prepare yourself for this battle with self-study! During this summer we will give you several tasks to boost your cyber knowledge in order to succeed in the final battle.
Enter the self-study portal here: https://portal.ctftech.io/
We are reminding you to register early for self-study and preliminar rounds to prepare yourself for the cyber battle. The self-study portal helps you to test your cyber skills.
Learn – Learning materials guide you through the topics that you need to know before you actually start practicing and solving challenges at the CTF Tech Portal. These materials support you throughout your journey with us and facilitate the learning process of ethical hackers. Different study modules are designed for users of different skill levels.
Play – CTF Tech Portal provides you an excellent opportunity to improve your cyber skills by solving different pracitcal tasks and challenges. In one way or another, the tasks are related to cyber incidents that have taken place in real life. Each task helps the player to develop their knowledge further on different cybersecurity topics (e.g. steganography, forensics, etc.).
Compete – CTF Tech Portal provides players opportunities to regularly challenge their cyber skills by competing against each other at CTF (capture-the-flag) type of competitions. Players can take part in both offline and online events, which test their cyber security expertise.
1.1. Self-learning Training Program
1.1.1. Approach
After bootcamps the participants will go through self-learning training program where they can put their freshly acquired skills into practice. The approach here is to provide participants the flexibility and time for solving the tasks. The self-learning program is divided into 2 phases:
1. Phase 1 – Hackers’ toolbox
2. Phase 2 – Tracing attackers
After Phase 1 and Phase 2 a Live Interactive Training Session is held where participants can learn about their successes and shortcomings and can ask additional questions from the cybersecurity professionals.
- CTF-type training – a gamified & engaging learning experience
In all three phases the participants are faced with jeopardy-style tasks that need to be solved by employing various cybersecurity skills to find clearly defined answers. As the name suggests, the expected answer can be nothing more than a simple “flag” that has no meaning of its own but is just a proof that a participant has been able to reach the desired goal. Participants are also presented with hints to help progressing through the task. The tasks are typically independent from each other, however there are options to group them based on topics or into a longer storyline that introduces dependencies. Such dependencies can be technically enforced on the platform, i.e., the next task in chain can be opened only after solving prerequisites, or once appropriate time has arrived.
1.1.2. Phase 1 – Hackers’ toolbox
- Overview
This module is meant to introduce the participants into the Jeopardy-style CTF tasks and get acquainted with Cyber Range functionality from this particular use-case perspective. The selection of tasks in this module is mainly aimed at the Novice audience who are just starting their journey in the cybersecurity field. This module can also be used in larger CTF events as a warm-up or entertaining component. The main goal is to make young people more cyber-savvy by providing them with knowledge in the cybersecurity field through practical cyber exercises. It also aims to introduce how working in the cyber world looks like and what are the relevant skills and knowledge required. The tasks in this module are accompanied with background stories to demonstrate a link with real-life use-cases and make the cybersecurity topics more appealing to newcomers.
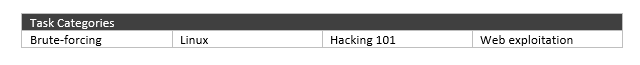
The tasks are intended for 6 hours and cover wide range of categories and offer the participants the experience of applying different skills.
- Objective
The objective of this self-learning module is to refresh the participants’ knowledges & skills of the preliminary bootcamp trainings and consolidate their newly acquired skills. The aim is to develop their individual skills in the chosen task categories.
- Live Interactive Training Session
This CTF module will be made available for the participants for a limited time period when they can access the tasks. After this, a curated training session with a cybersecurity professional is held where the tasks are briefly explained, and participants can ask questions.
1.1.3. Phase 2 – Tracing attackers
- Overview
This module is meant to introduce the participants to the tools the defenders use and enhance the skillset of using open-source tools such as Security Onion, ELK-stack, Graylog Log Management platform, Arkime Network Packet Capture, etc. Similarly to Phase 1, the participants are faced with jeopardy-style practical tasks where the answer can be nothing more than a simple “flag” that has no meaning on its own but is just a proof that the participant has been able to reach the desired goal.
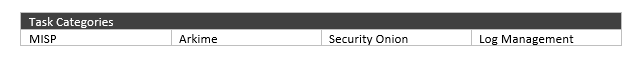
The tasks are intended for 2 hours and cover wide range of categories and offer the participants the experience of applying different skills.
- Objective
The objective of this self-learning module is to prepare the participants for the finals. Within this module participants learn about the open-source tools that the defenders use.
- Live Interactive Training Session
This CTF module will be made available for the participants for a limited time period when they can access the tasks. After this, a curated training session with a cybersecurity professional is held where the tasks are briefly explained, and participants can ask questions.